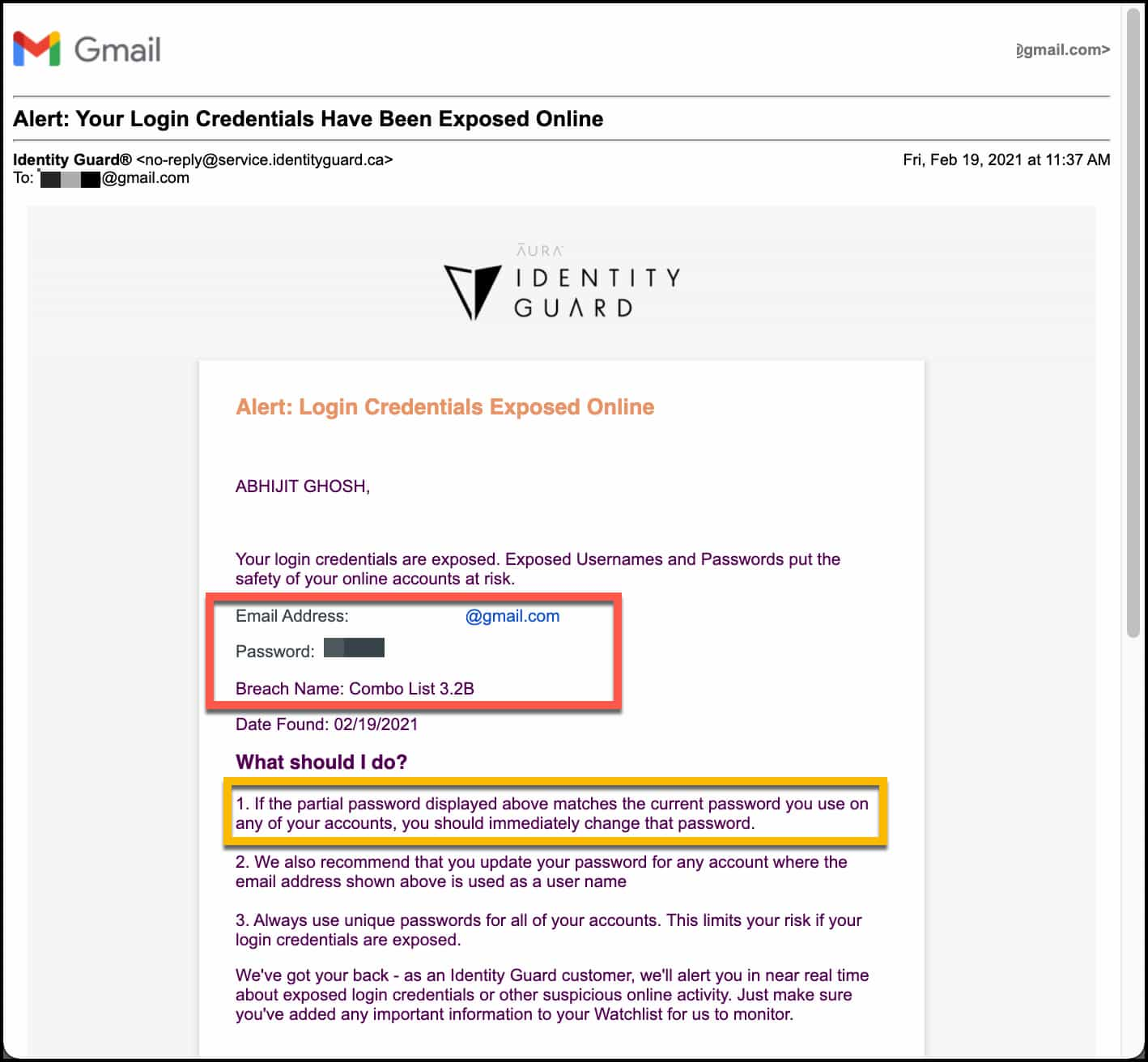
"No News is Good News". That is what I used to get from Identity Guard®. But yesterday, I got email & sms notification "Alert: Your Login Credentials Have Been Exposed Online". And partial password shared in that notification is actually matching with my credentials. So, mine got exposed. Check yours.
What is "Breach Combo List 3.2B" ?
"COMB List 3.2B" is a compilation of many breaches. 3.2 billions loginid and password has been published in plain text format. It contains billions of login credentials from LinkedIn, Netflix, Exploit.in and many more from past breaches. 3.2 billions is massive considering 4.66 billion active internet users worldwide.
How many people use the internet?"
As of January 2021 there were 4.66 billion active internet users worldwide - 59.5 percent of the global population. Of this total, 92.6 percent (4.32 billion) accessed the internet via mobile devices."
Source: statista.com
I always use separate set of emails & password combinations for email communication, banking sites, major social media sites and third party OAuth. Based on the below combination, I easily identified that my LinkedIn login credentials got exposed on the Dark Web in this mind-boggling breach.
Market research company "CyberNews" has provided a online tool "Personal Data Leak Checker". It has 500 GB database (15 billion compromised accounts) of hashed emails that have been leaked over time.
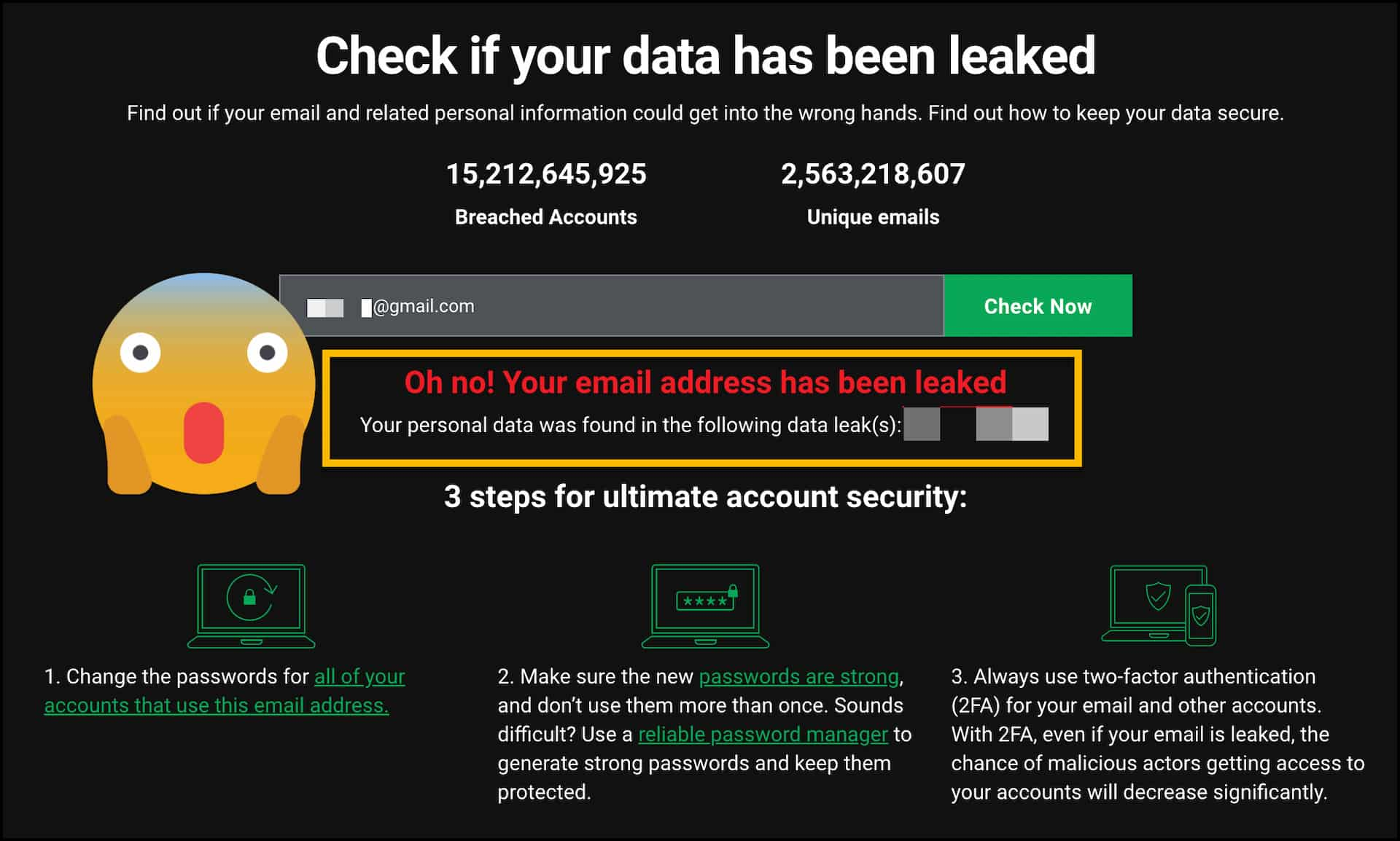
How does this tool work?
Our checker has a 500 GB database of hashed emails that have been leaked. To check if your email address was leaked:
- You enter the email address in the search field. Your email is not collected, logged or stored
- The tool hashes the email you entered and uses only this hash to perform a search in our database
- The search results appear on the same page
Source: https://cybernews.com/personal-data-leak-check/
How do we store data from breaches?
Our database contains nothing more than the email address and the source of the leak. All information in our database is hashed with Blowfish based crypt (bcrypt) hashing algorithm. It is one of the safest hashing algorithms. All emails are anonymised and linked only to the source of the leak.
What happens when you check if your data has been leaked?
The email address that you enter in the search field is hashed and we use only this hash to perform a search in our database. We do not collect entered emails, nothing is logged when you perform the data leak check.
Source: Leak check FAQ
Many of us use the same email id for communication, social sites, banking sites etc. Sometime, same password everywhere. It is an unsafe practice.
The SMS breach alert got me worried, but it did not have catastrophic consequences for me. Solely because I use different set of credentials for all major sites / applications and always enable Multi-Factor Authentication (MFA) or 2-step verification. Even if someone has access to my credentials, One-Time-Password (OTP) / second level of verification will work as second line of defence. This significantly reduces limits the risk if your login credentials are exposed on Dark Web.
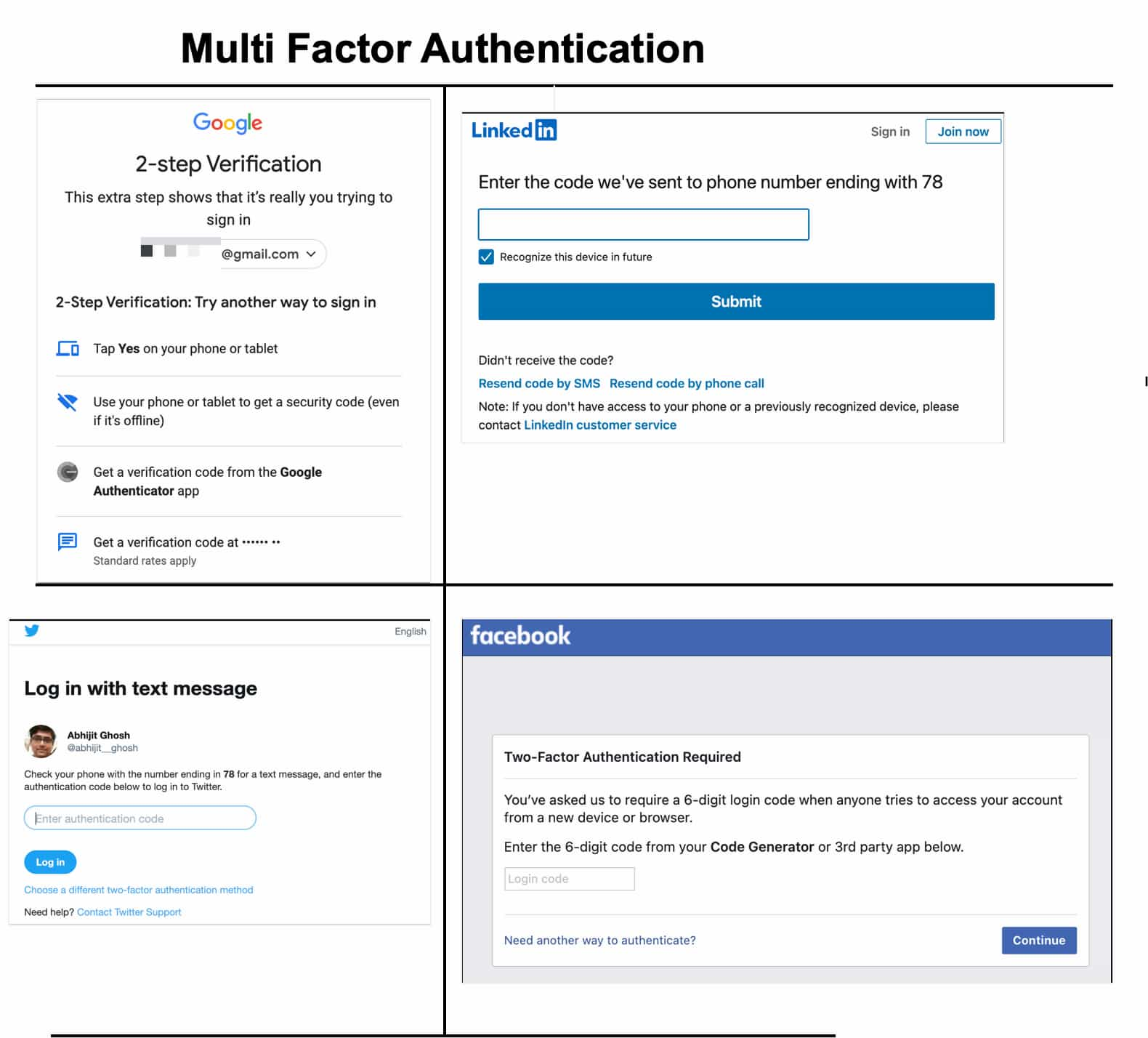
Sharing few recommendations that I received from Identity Guard® along with the security alert.
What should I do?
- We recommend that you update your password for any account where the email address shown in your alert is used as a user name.
- Always use unique passwords for all of your accounts. This limits your risk if your login credentials are exposed.
- Consider activating multi-factor authentication—which means your password in addition to one or more other means of authentication—on any account that allow this option. Multi-factor authentication is the best way to keep your accounts more secure.
Source: Identity Guard® FAQ
Gmail, Facebook, Twitter, LinkedIn, etc. all are amazing services. We mostly don't pay anything directly to them. It is absolutely free, if one is gone, we can open another one. But reality is beyond this. If we loose access, it may create huge damage in terms of reputation, financially or inconvenience based on kind of user we are and our usage pattern.

Comments